ssh 反代
https://zhuanlan.zhihu.com/p/34908698
https://zaiste.net/ssh_port_forwarding/
這個動態有錯,測試不出來 (D 後查資料,變成是proxy socket方式,給porxy使用,這裡不需要這個設定)
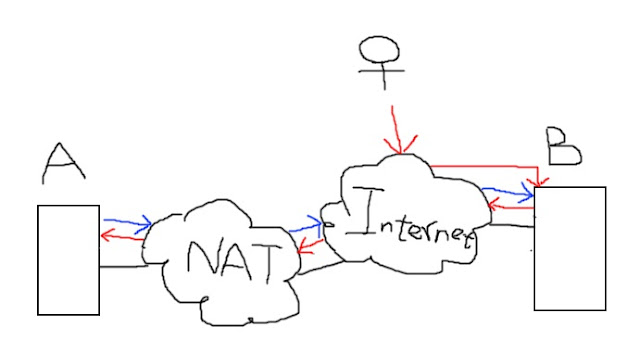
內網主機A 外網主機B
內網主機A 設定:
ssh -NR 20000:localhost:80 xxxx@xxx.ooo.xxx.ooo
20000: 遠端打算 打開的port
localhost:80 :指目前 內網主機A上的服務port,或是其他主機和port也可以,只要是A主機連得到的
xxx :B user id
xxx.ooo.xxx.ooo :B ip
PS:這個連上後,可以在 B上試 curl localhost:20000是否會通,不通則代表沒有建立成功或是該服務不接受連線,測試連線位址只限用localhost本地
PS:-g是別人(所有人)可以連,但 -NR + g => -gNR 經測試是無效的
外網主機B:
這裡最主要目的是開放 20000開放讓所有人可以連,但實際上2000已經被反向代理使用中,也被限制住了(localhost),所以
變成 開放 30002 讓別人(所有人)可以連,透過30002轉向20000
ssh -gL 30002:localhost:20000 localhost
-gL : -g 開放給別人連(所有人):這裡和教學不同,教學用D,試是失敗的 (D 後查資料,變成是proxy socket方式,給porxy使用,這裡不需要這個設定)
30002: 指外網主機B 打算開那個port 給人用
localhost: 這裡指的都是 外網主機B
20000:最上面操作時,在外網主機B 開的port
A 80 -> B 20000 <-> 30002 <- outside people
The -nNT flags will cause SSH to not allocate a tty and only do the port forwarding.
$ ssh -nNT -L 9000:imgur.com:80 user@example.com
======
https://superuser.com/questions/408031/differences-between-ssh-l-to-d
https://explainshell.com/explain?cmd=ssh+-L+-N+-f+-l
Differences between ssh -L to -D
ssh -L opens a local port. Everything that you send to that port is put through the ssh connection and leaves through the server. If you do, e.g., ssh -L 4444:google.com:80, if you open http://localhost:4444 on your browser, you’ll actually see google’s page.
ssh -D opens a local port, but it doesn’t have a specific endpoint like with -L. Instead, it pretends to be a SOCKS proxy. If you open, e.g., ssh -D 7777, when you tell your browser to use localhost:7777 as your SOCKS proxy, everything your browser requests goes through the ssh tunnel. To the public internet, it’s as if you were browsing from your ssh server instead of from your computer.
Specifies a local “dynamic” application-level port forwarding. This works by allocating a socket to listen to port on the local side, optionally bound to the specified bind_address. Whenever a connection is made to this port, the connection is forwarded over the secure channel, and the application protocol is then used to determine where to connect to from the remote machine. Currently the SOCKS4 and SOCKS5 protocols are supported, and ssh will act as a SOCKS server. Only root can forward privileged ports. Dynamic port forwardings can also be specified in the configuration file.
==== become ssh tunnel service
https://kauri.io/make-use-of-your-remote-ethereum-node-using-an-ssh-tunnel-and-metamask/348d6c66da2949978c85bf2cd913d0ac/a
$ cat > persistent.ssh.tunnel.service <<EOF
[Unit]
Description=Persistent SSH Tunnel
[Service]
User=user
Type=simple
Restart=always
ExecStartPre=/bin/sleep 10
ExecStart=/usr/bin/ssh -N -v user@172.16.389.54 -L 8545:localhost:8545
[Install]
WantedBy=default.target
EOF
$ sudo mv persistent.ssh.tunnel.service /etc/systemd/system/
$ sudo systemctl daemon-reload
$ sudo systemctl enable persistent.ssh.tunnel.service
$ sudo systemctl start persistent.ssh.tunnel.service
sudo systemctl status persistent.ssh.tunnel.service